In a fast-paced DevOps world, speed is everything—until compliance becomes an afterthought. For organizations bound by regulatory requirements like GDPR, HIPAA, SOC 2, or PCI-DSS, overlooking compliance can lead to legal, financial, and reputational risks.
But here’s the good news: compliance doesn’t have to slow you down. By integrating compliance checks directly into your CI/CD pipeline, you can ensure your code, infrastructure, and configurations meet policy standards continuously—without sacrificing agility.
This blog explores the principles of continuous compliance, practical implementation methods, and how to build pipelines that are both fast and compliant by design.
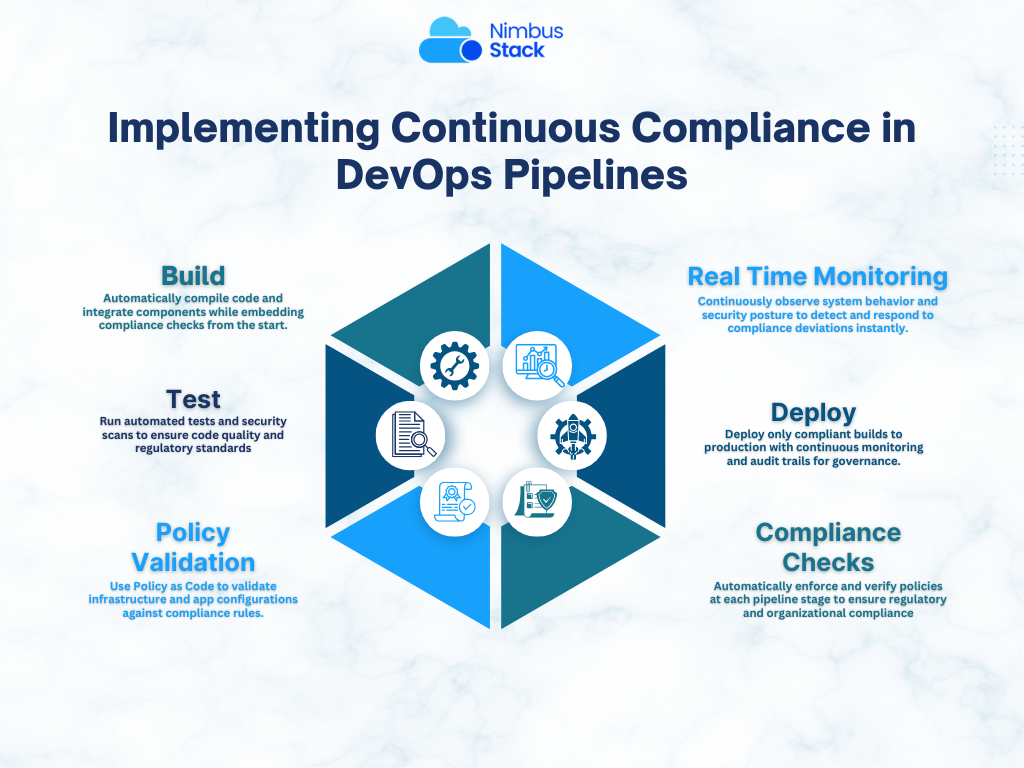
What Is Continuous Compliance?
Continuous compliance is the practice of embedding compliance validations into every phase of the DevOps lifecycle—from code commit to deployment. Instead of periodic audits or manual reviews, checks are automated, version-controlled, and run in real time.
Think of it as shift-left compliance—where policies are enforced as early as possible, just like security in DevSecOps.
Why It Matters
- Avoid costly rework: Catching misconfigurations or non-compliant code early saves time and effort.
- Improve audit readiness: Compliance artifacts are logged and versioned as part of the delivery process.
- Reduce manual reviews: Automating controls minimizes reliance on human checklists.
- Enable secure velocity: Developers ship fast, while compliance is built in—not bolted on.
What to Monitor for Compliance?
Depending on your industry, you’ll need to monitor different aspects of your pipeline and infrastructure, such as:
- Infrastructure provisioning: Are resources encrypted? Are security groups overly permissive?
- Code quality and dependencies: Are there known vulnerabilities or license violations?
- Data privacy: Is sensitive data being logged or exposed?
- User access control: Are IAM roles scoped properly? Are secrets hardcoded?
- Network configuration: Are ports, APIs, and endpoints appropriately restricted?
Key Components of a Continuous Compliance Strategy
1. Policy as Code (PaC)
Define your compliance rules in code using tools that can evaluate infrastructure and application configurations automatically.
Popular Tools:
- HashiCorp Sentinel: PaC for Terraform and Vault.
- Open Policy Agent (OPA): Policy engine for Kubernetes, APIs, CI/CD, and more.
- AWS Config + AWS Config Rules: Automates compliance checks for AWS resources.
2. Integrate Compliance into CI/CD Workflows
Add policy validation steps into your pipeline, just like linting or unit tests.
CI/CD Integration Examples:
- Run OPA Gatekeeper during kubectl apply to validate Kubernetes manifests.
- Validate Terraform plans using Sentinel or Checkov before applying.
- Use GitHub Actions or GitLab CI to scan Docker images, dependencies, and secrets.
3. Use Infrastructure as Code (IaC)
IaC ensures consistent, version-controlled infrastructure that can be reviewed and validated like application code.
Best Practices:
- Use Terraform or Pulumi to manage cloud resources.
- Validate configurations with tfsec, Checkov, or CloudFormation Guard.
- Enforce reviews on infrastructure pull requests for changes to critical configurations.
4. Monitor and Remediate in Real Time
Use continuous monitoring to catch and correct drift or policy violations post-deployment.
Example Tools:
- AWS Config or Azure Policy to detect configuration drift.
- Falco to monitor Kubernetes runtime behavior.
- Steampipe to run SQL-based compliance queries across cloud accounts.
5. Generate and Store Evidence Automatically
Compliance isn’t just about enforcing rules—it’s also about proving you did.
- Archive logs, test results, and policy validation outputs to S3, GCS, or a secure compliance vault.
- Use tools like Auditd, AWS CloudTrail, or Azure Monitor for traceability.
- Automate compliance report generation with dashboards for auditors and stakeholders.
Real-World Example: PCI Compliance in a CI/CD Pipeline
A payments company required PCI DSS compliance for deploying applications on AWS. They implemented:
- Terraform with Sentinel policies to ensure encryption and network rules.
- Pre-deploy OPA checks in GitHub Actions for Kubernetes manifests.
- Automated secrets scanning using truffleHog.
- CloudTrail logs + Amazon Athena to audit access control and data flows.
As a result, deployments remained compliant without slowing down delivery, and audit preparation dropped from weeks to days.
Challenges and How to Overcome Them
| Challenge | Solution |
| Developer pushback on “gatekeeping” | Involve teams in policy creation and provide clear feedback in pipelines |
| Overhead from false positives | Tune rules and implement tiered alerting |
| Policy sprawl and maintenance | Consolidate rules in shared, versioned repositories |
| Keeping up with evolving standards | Subscribe to regulatory feeds and integrate updates into your policy lifecycle |
Best Practices for Continuous Compliance
- Start small, scale fast: Begin with critical policies and expand coverage gradually.
- Test locally: Validate policies during development before hitting the pipeline.
- Automate feedback loops: Provide real-time, actionable results to developers.
- Make compliance visible: Use dashboards and alerts to foster transparency.
- Treat compliance like code: Review, test, and evolve your policies with the same rigor as your software.
Conclusion
Compliance doesn’t have to be a blocker in your DevOps pipeline. By treating policies as code, integrating validations into CI/CD, and continuously monitoring infrastructure, teams can ship fast and stay compliant.
With the right tooling and culture, continuous compliance becomes a strategic enabler—not a burden. Whether you’re preparing for your next audit or preventing the next breach, embedding compliance into your pipeline is the future of secure, reliable cloud development.