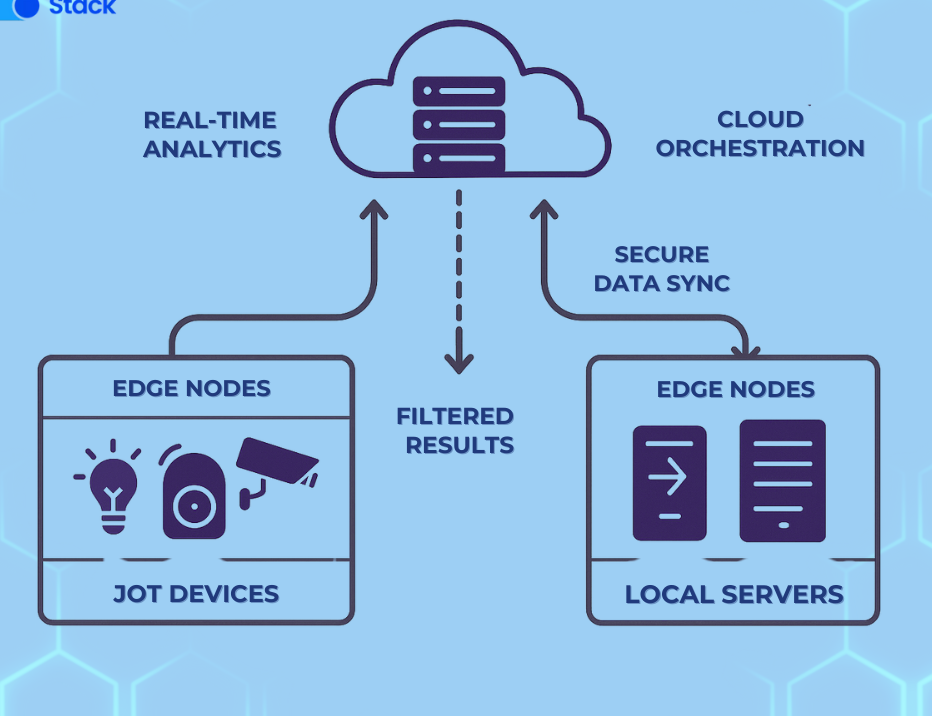
As microservices architectures grow in complexity, managing how services interact becomes increasingly challenging. Traditional approaches to service-to-service communication—once manageable in monolithic systems—now struggle to meet the demands of modern, distributed applications. That’s where service meshes come into play.
A service mesh offers a powerful abstraction layer that manages how microservices discover, connect, secure, and monitor each other—without developers having to build those capabilities into each service.
In this blog, we’ll explore what a service mesh is, how it works, and why it’s becoming essential for managing microservices communication in cloud-native environments.
What Is a Service Mesh?
A service mesh is an infrastructure layer that manages east-west traffic—the internal communication between services in a distributed application. It offloads cross-cutting concerns such as service discovery, traffic management, observability, and security from application code to the platform layer.
At its core, a service mesh uses sidecar proxies—usually deployed alongside each service instance—to intercept and manage network traffic.
Popular service meshes include:
- Istio (often used with Kubernetes)
- Linkerd
- Consul Connect
- AWS App Mesh
- Open Service Mesh (OSM)
Why Microservices Need a Service Mesh
In microservices architectures, you often deal with:
- Dozens or hundreds of independently deployable services.
- Dynamic scaling and shifting of service endpoints.
- Complex traffic flows with retries, timeouts, and failover logic.
- The need for encryption and access control between services.
Without a service mesh, teams typically handle these concerns at the application level, resulting in duplicated effort, increased risk, and operational complexity.
Core Capabilities of a Service Mesh
Let’s break down the essential features that service meshes provide—and how they solve real-world problems.
1. Secure Communication (mTLS)
Service meshes automatically encrypt service-to-service communication using mutual TLS (mTLS). This ensures that traffic is encrypted and that both parties are authenticated.
Benefit: Strong zero-trust security posture without manual certificate management.
2. Fine-Grained Traffic Control
Service meshes allow granular control over traffic routing, enabling:
- Canary releases
- Blue/green deployments
- A/B testing
- Traffic mirroring
Benefit: Safer deployments with real-time testing and rollback capabilities.
3. Service Discovery and Load Balancing
Instead of relying on hardcoded IPs or custom DNS logic, service meshes dynamically discover and route traffic to healthy instances.
Benefit: Improved reliability and reduced complexity in handling service lifecycles.
4. Observability and Telemetry
Service meshes provide built-in telemetry by collecting metrics, logs, and traces from every service interaction—often integrated with tools like Prometheus, Grafana, Jaeger, or OpenTelemetry.
Benefit: Deep visibility into traffic flows, performance bottlenecks, and error rates.
5. Resilience and Reliability
Service meshes can enforce retry policies, circuit breakers, timeouts, and rate limits—ensuring graceful degradation when failures occur.
Benefit: Improved service uptime and user experience during partial outages.
How a Service Mesh Works: The Sidecar Pattern
The most common implementation pattern is the sidecar proxy. Here’s how it works:
- Each microservice instance is paired with a proxy (like Envoy).
- All inbound and outbound traffic flows through the proxy.
- The control plane (e.g., Istio’s Pilot or Consul’s Control Plane) configures these proxies with rules and policies.
This design decouples traffic management from application logic, enabling teams to apply changes across services without touching the codebase.
Service Mesh in Action: A Real-World Example
Scenario: Online Retail Platform on Kubernetes
A cloud-native retail application uses microservices for checkout, inventory, user accounts, and recommendation engines.
With a service mesh (Istio):
- mTLS secures sensitive traffic between checkout and payment services.
- Canary deployments are used to test a new recommendation algorithm on 10% of users.
- Prometheus and Grafana dashboards monitor latency and error rates across services.
- Rate limiting protects the inventory service during peak sale events.
- Circuit breakers ensure user sessions are maintained even if the recommendations service fails.
When to Use a Service Mesh
Ideal Scenarios:
- Kubernetes-based microservices with complex traffic patterns.
- Applications requiring strict inter-service security policies.
- Environments needing high observability and auditability.
- Teams embracing GitOps, progressive delivery, and infrastructure as code.
Challenges of Adopting a Service Mesh
| Challenge | Mitigation |
| Steep learning curve | Start with a minimal mesh (e.g., Linkerd), scale capabilities gradually |
| Operational overhead | Use managed services like AWS App Mesh or Anthos Service Mesh |
| Added latency | Optimize proxy configuration and monitor overhead |
| Policy sprawl | Maintain versioned policies as code and centralize governance |
Best Practices for Implementing a Service Mesh
- Start small: Roll out in a non-critical namespace or environment.
- Adopt a “mesh team”: Assign champions from DevOps, security, and SRE to lead adoption.
- Automate policy management: Store traffic and security rules in Git and apply via CI/CD.
- Instrument early: Integrate observability tooling from day one.
- Use managed offerings when possible: Reduce complexity with cloud-native service mesh solutions.
Conclusion
Service meshes are becoming a critical piece of cloud-native architecture, especially as microservices scale. By offloading service communication concerns—like security, traffic routing, and observability—from your code to a dedicated mesh layer, you gain control, insight, and reliability without adding application-level complexity.
While not every application needs a service mesh, for teams managing large-scale microservices in Kubernetes or hybrid clouds, the benefits are clear.