Maintaining compliance in the cloud is critical for ensuring security, governance, and adherence to industry standards. AWS Config, combined with AWS Lambda, provides a powerful solution for automating compliance monitoring in your AWS environment. By continuously tracking resource configurations and validating them against custom rules, this setup helps ensure that your infrastructure remains compliant with organizational and regulatory policies.
This blog explores how AWS Config and Lambda work together to automate compliance checks, highlights common use cases, and offers best practices for implementation.
The Importance of Cloud Compliance Monitoring
As organizations migrate to the cloud, the dynamic nature of cloud resources makes it challenging to maintain compliance. Without robust monitoring, non-compliant resources can introduce security vulnerabilities, operational inefficiencies, and regulatory risks.
Automating compliance monitoring provides several benefits:
- Continuous Validation: Automatically detect and report non-compliant configurations.
- Reduced Manual Effort: Eliminate repetitive tasks with automated rule enforcement.
- Improved Security Posture: Proactively address misconfigurations before they lead to breaches.
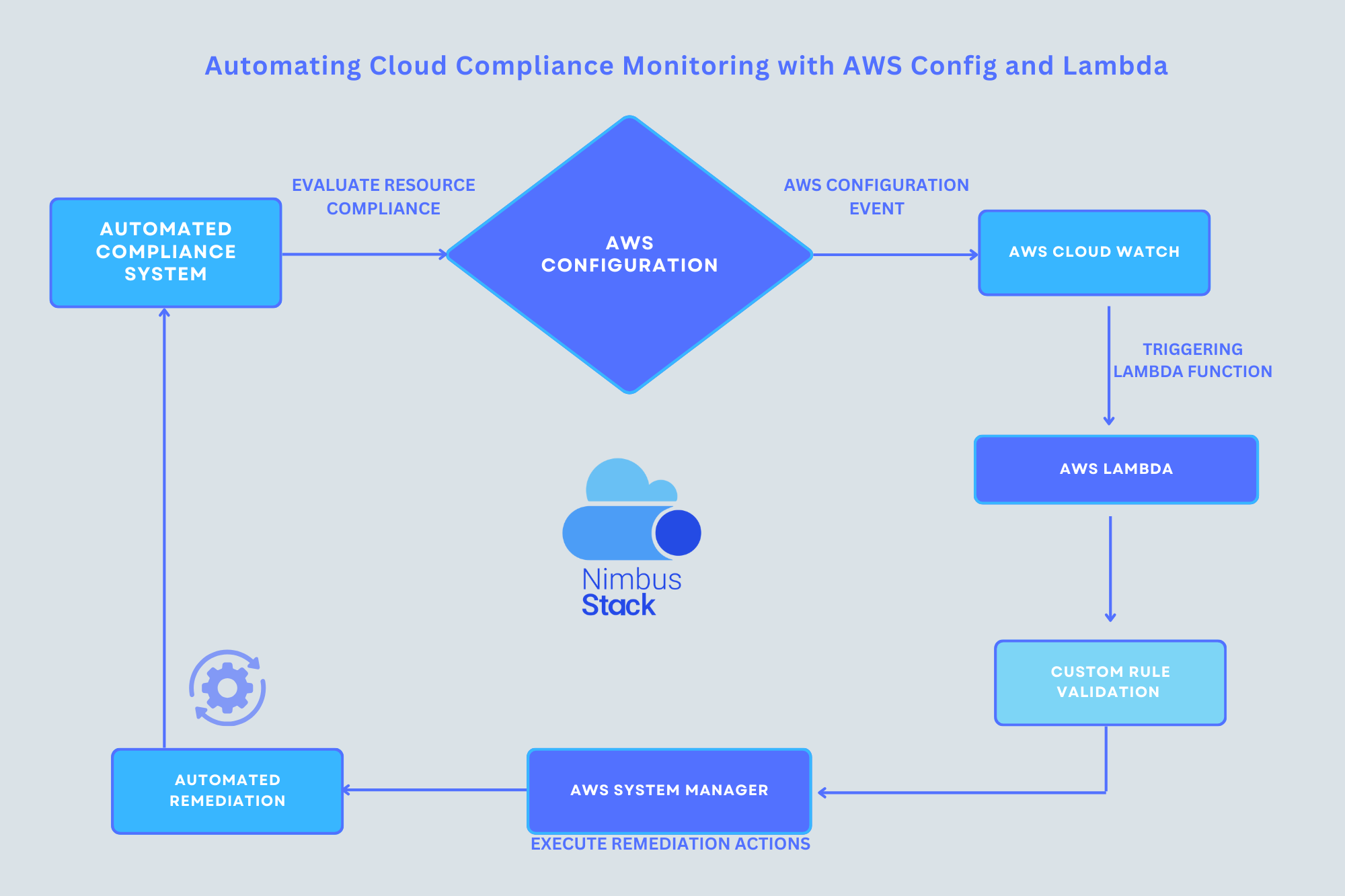
How AWS Config and Lambda Work Together
AWS Config: Continuous Resource Monitoring
AWS Config is a service that records configuration changes for your AWS resources. It evaluates these configurations against predefined or custom compliance rules and generates compliance reports.
AWS Lambda: Custom Rule Execution
AWS Lambda allows you to execute custom logic in response to triggers. When paired with AWS Config, Lambda can:
- Evaluate resource configurations against custom criteria.
- Remediate non-compliant resources by applying corrective actions.
Automating Compliance Checks: Step-by-Step
Step 1: Enable AWS Config
- Open the AWS Config console.
- Select the resources you want to monitor (e.g., EC2 instances, S3 buckets).
- Enable configuration recording for the chosen resources.
- Configure an S3 bucket to store resource configuration snapshots.
Step 2: Define AWS Config Rules
AWS Config provides two types of rules:
- Managed Rules: Predefined rules from AWS (e.g., checking if S3 buckets have encryption enabled).
- Custom Rules: User-defined rules using Lambda functions.
Example Managed Rule:
- Rule Name:
s3-bucket-public-read-prohibited - Description: Ensures no S3 bucket is publicly accessible.
Step 3: Create a Custom Rule with Lambda
For scenarios not covered by managed rules, you can create custom rules.
Example Use Case: Ensure EC2 Instances Have Specific Tags
Write a Lambda Function:
python:
import json
def evaluate_compliance(event, context):
evaluations = []
for resource in event['invokingEvent']['configurationItems']:
if 'Environment' in resource.get('tags', {}):
compliance_type = 'COMPLIANT'
else:
compliance_type = 'NON_COMPLIANT'
evaluations.append({
"ComplianceResourceType": resource['resourceType'],
"ComplianceResourceId": resource['resourceId'],
"ComplianceType": compliance_type,
"Annotation": "Environment tag is missing" if compliance_type == 'NON_COMPLIANT' else ""
})
return evaluations
- Deploy the Function: Use the AWS Lambda console to upload your function and assign it an IAM role with appropriate permissions.
- Integrate with AWS Config: Link the Lambda function to your AWS Config rule.
Step 4: Automate Remediation
Use AWS Lambda or Systems Manager to automatically remediate non-compliant resources. For instance:
- Enable encryption on an unencrypted S3 bucket.
- Stop or terminate non-compliant EC2 instances.
Common Use Cases for AWS Config and Lambda
1. Security and Governance
- Ensure S3 buckets have encryption enabled.
- Verify that EC2 instances are using approved AMIs.
2. Cost Optimization
- Check for unused EBS volumes and terminate them.
- Identify idle or underutilized EC2 instances.
3. Operational Best Practices
- Ensure resources are tagged correctly for billing and management.
- Validate that IAM roles adhere to least-privilege principles.
Benefits of Automating Compliance Monitoring
- Real-Time Visibility: Gain immediate insights into compliance status with AWS Config dashboards.
- Customizability: Tailor compliance checks to your organization’s unique policies using Lambda.
- Scalability: Automate compliance checks across multiple AWS accounts and regions.
- Cost Efficiency: Reduce manual audits and streamline remediation processes.
Challenges and Solutions
1. Managing Custom Rules
- Challenge: Writing and maintaining custom Lambda functions can be time-consuming.
- Solution: Modularize your Lambda functions and reuse components where possible.
2. Cross-Account Compliance
- Challenge: Ensuring compliance in multi-account environments.
- Solution: Use AWS Organizations and Config Aggregators to centralize compliance monitoring.
3. Large-Scale Remediation
- Challenge: Automated remediation at scale can inadvertently impact critical resources.
- Solution: Implement approval workflows for high-impact remediation actions.
Best Practices for Implementing Compliance Monitoring
- Leverage Managed Rules First: Use AWS’s managed rules whenever possible to save time and effort.
- Test Custom Rules Thoroughly: Validate Lambda functions in a non-production environment before deploying them.
- Centralize Monitoring: Use Config Aggregators to monitor compliance across multiple accounts and regions.
- Integrate with CloudWatch Alarms: Set up alarms for critical non-compliance events to notify your team immediately.
- Audit Regularly: Use AWS Config’s compliance reports for periodic reviews and audits.
Real-World Applications
1. Financial Services Compliance
A financial institution uses AWS Config to ensure encryption is enabled on all data storage resources, and Lambda automatically remediates non-compliant configurations.
2. Healthcare Data Protection
A healthcare provider leverages AWS Config to validate HIPAA compliance, ensuring that sensitive data is encrypted and access controls are in place.
3. DevOps Governance
A DevOps team uses AWS Config rules to enforce resource tagging policies and track unapproved changes to infrastructure.
Conclusion
AWS Config and Lambda empower organizations to automate compliance monitoring in cloud environments, ensuring adherence to security, governance, and regulatory standards. By combining the continuous monitoring of AWS Config with the flexibility of Lambda, you can build a robust compliance solution tailored to your organization’s needs.