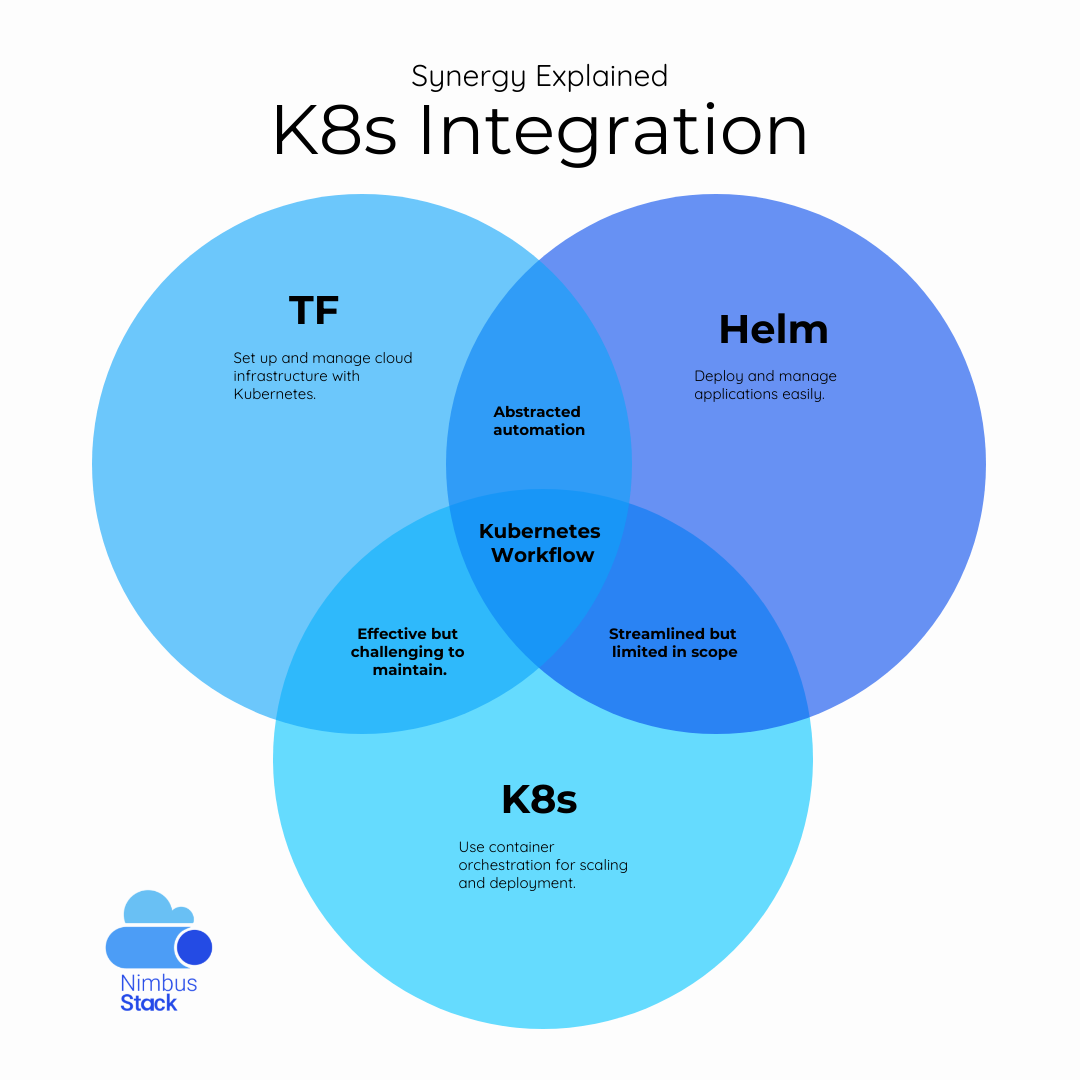
When managing Kubernetes-based applications and infrastructure, two powerful tools stand out: Helm and Terraform. Helm simplifies the deployment of applications in Kubernetes, while Terraform excels at managing infrastructure as code. Combining these tools can lead to a seamless, efficient, and scalable DevOps workflow.
In this article, we’ll explore how to integrate Helm and Terraform effectively, with actionable steps, practical use cases, and expert tips.
Why Combine Helm and Terraform?
Helm: Simplifying Kubernetes Deployments
Helm charts are packaged templates of Kubernetes manifests. They:
- Reduce boilerplate configuration.
- Simplify upgrades and rollbacks.
- Provide parameterized deployment flexibility.
Terraform: Infrastructure as Code (IaC)
Terraform allows you to provision infrastructure resources declaratively. It:
- Manages cloud and on-prem infrastructure.
- Tracks changes through a state file.
- Offers modular and reusable configuration.
The Benefits of Integration
- End-to-End Automation: Use Terraform to provision cloud resources and Helm to deploy applications, ensuring consistency across the pipeline.
- Unified State Management: Terraform tracks Kubernetes and non-Kubernetes resources in a single state.
- Scalability: Streamline complex infrastructure and application deployments across multiple environments.
How to Integrate Helm and Terraform
Here’s a step-by-step guide:
Step 1: Set Up Terraform Provider for Kubernetes
Terraform requires a Kubernetes provider to interact with your cluster.
hcl
provider “kubernetes” {
config_path = “~/.kube/config”
}
Step 2: Use the Helm Provider
Terraform includes a Helm provider, enabling you to manage Helm charts directly.
hcl
provider “helm” {
kubernetes {
config_path = “~/.kube/config”
}
}
Step 3: Deploy Helm Charts with Terraform
You can deploy a Helm chart by specifying its source (e.g., a public chart repository or a local directory).
hcl
resource “helm_release” “nginx” {
name = “nginx”
chart = “nginx”
repository = “https://charts.bitnami.com/bitnami”
namespace = “default”
values = [
file(“${path.module}/values.yaml”)
]
}
Step 4: Combine Terraform Modules and Helm Releases
Modularize your configuration by separating infrastructure (e.g., cloud resources) and Kubernetes applications into distinct Terraform modules.
- Infrastructure Module: Provisions cloud resources like VPCs, subnets, and EKS clusters.
- Helm Module: Deploys applications into the cluster.
Example Directory Structure:
css
modules/
├── infrastructure/
│ ├── main.tf
│ └── variables.tf
├── helm/
├── main.tf
├── values.yaml
└── variables.tf
Step 5: Manage Dependencies
To ensure proper sequencing:
- Use the depends_on argument in Terraform to define dependencies between modules.
Apply configurations incrementally:
bash
terraform apply -target=module.infrastructure
terraform apply
Use Cases of Helm and Terraform Integration
- Multi-Cloud Deployments
Use Terraform to provision Kubernetes clusters across multiple cloud providers (e.g., AWS, Azure, GCP) and Helm to deploy identical workloads. - CI/CD Pipelines
Automate the deployment of Helm charts using Terraform in a CI/CD pipeline. For example:- Terraform provisions the infrastructure.
- Helm charts configure the application and its dependencies.
- Disaster Recovery
Store your Terraform and Helm configurations in version-controlled repositories, enabling rapid recovery of both infrastructure and applications.
Best Practices
- Separate State Files: Use separate Terraform state files for infrastructure and application configurations to avoid conflicts.
- Leverage Terraform Workspaces: Isolate environments (e.g., dev, staging, production) using Terraform workspaces.
- Define Clear Boundaries: Use Terraform for resource provisioning and Helm for application deployment.
- Secure Secrets: Manage sensitive information (e.g., database passwords) using tools like HashiCorp Vault or Kubernetes Secrets.
Challenges and How to Address Them
- Complex Dependencies: Use Terraform’s depends_on to enforce resource creation order.
- State Drift: Regularly run terraform plan to detect configuration drift.
- Debugging Failures: Use Terraform logs and Helm’s –debug flag for troubleshooting.
Final Thoughts
Integrating Helm and Terraform bridges the gap between Kubernetes application management and infrastructure provisioning. By adopting this approach, you can achieve a robust, automated, and scalable DevOps pipeline. Whether you’re deploying microservices, managing multi-cloud environments, or streamlining CI/CD workflows, this combination empowers your team to deliver efficiently.