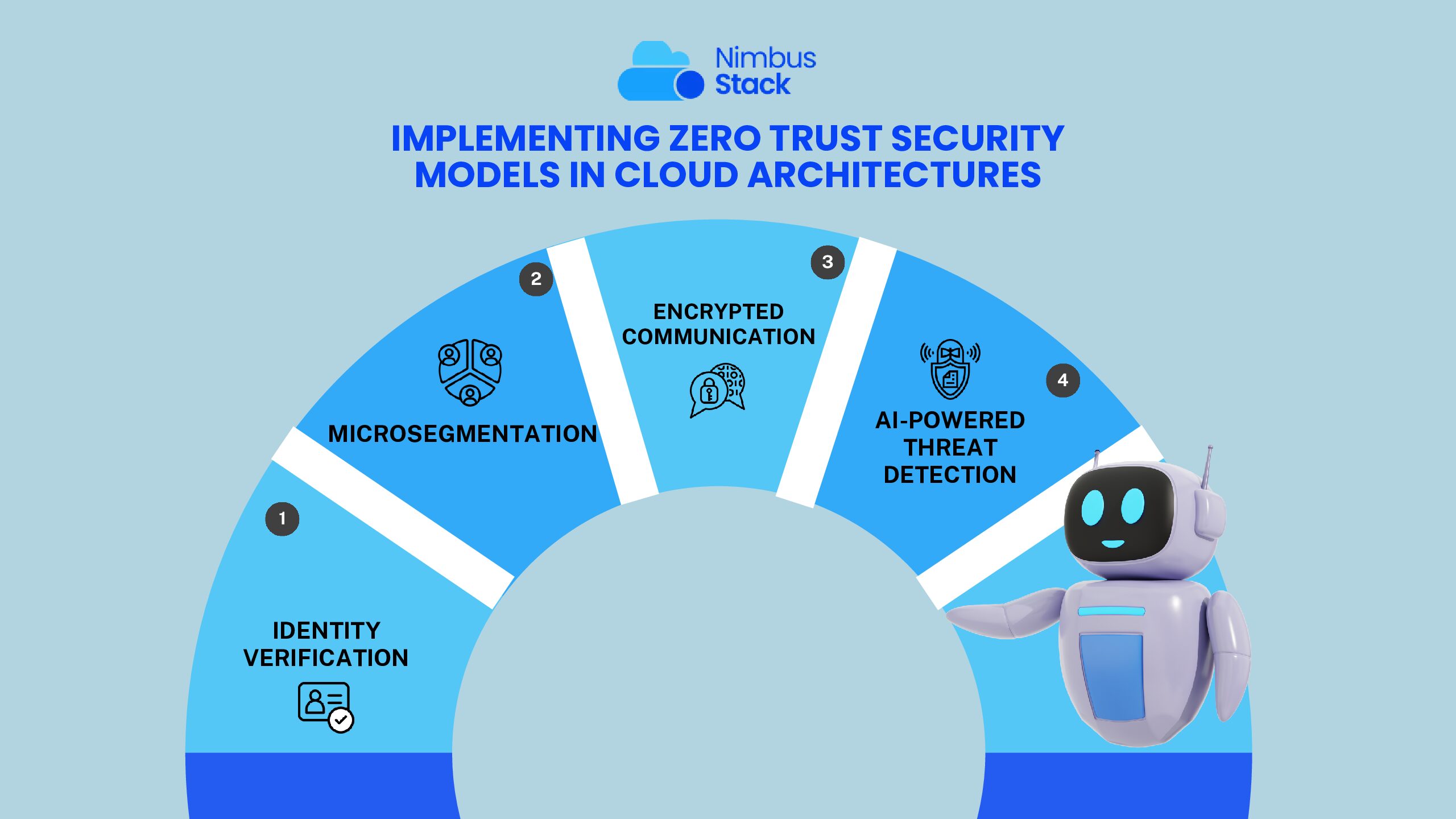
Gone are the days when firewalls and perimeter-based security models were enough to protect your infrastructure. In the cloud, where users, data, and workloads move dynamically across networks and services, Zero Trust is no longer optional—it’s essential. Zero Trust Security operates on a powerf...
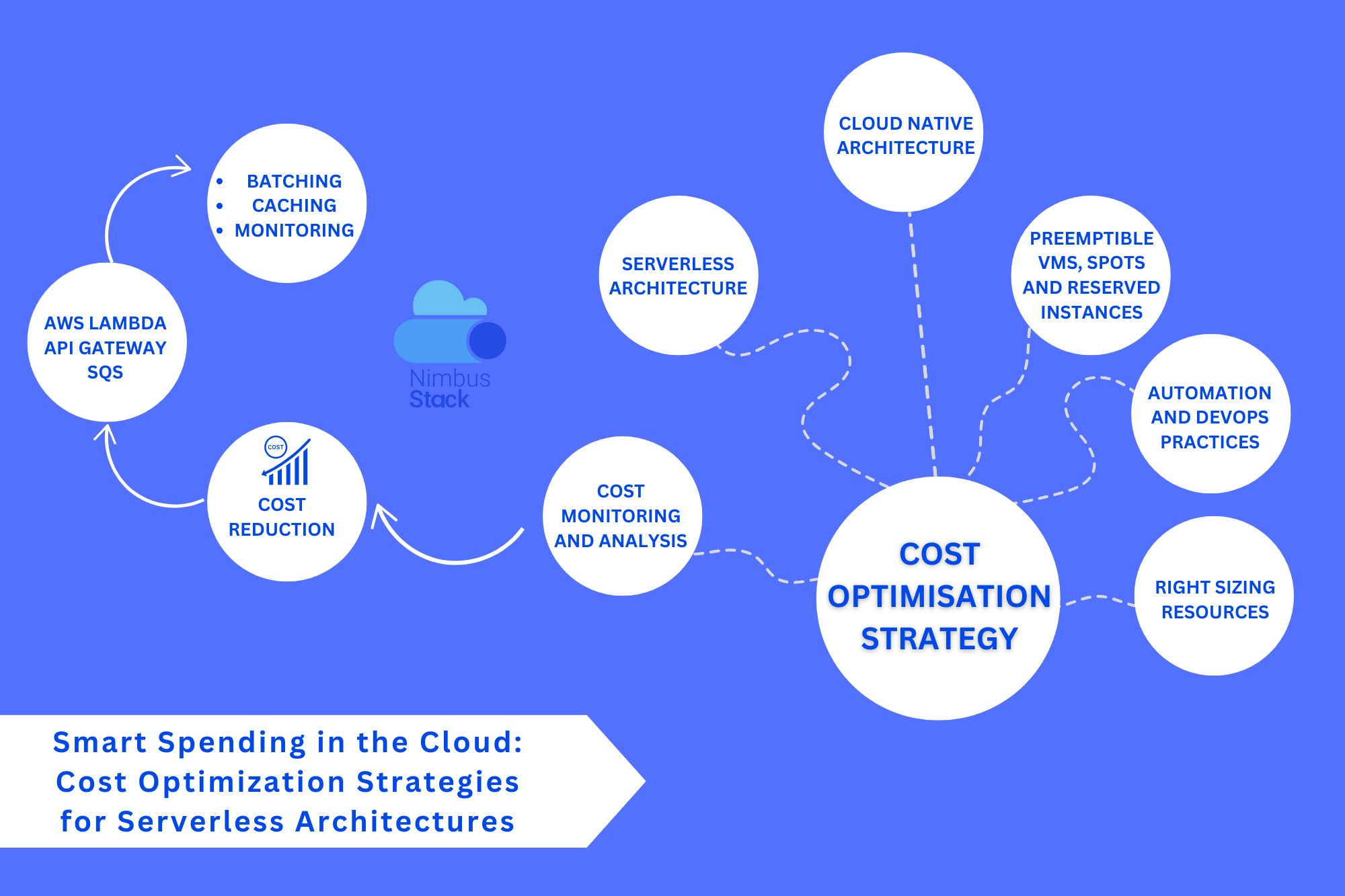
Optimization Strategies for Serverless Architectures Serverless architectures have transformed how we build and deploy applications, offering unparalleled scalability and reduced operational overhead. However, the “pay-as-you-go” model that makes serverless appealing can quickly lead to ...
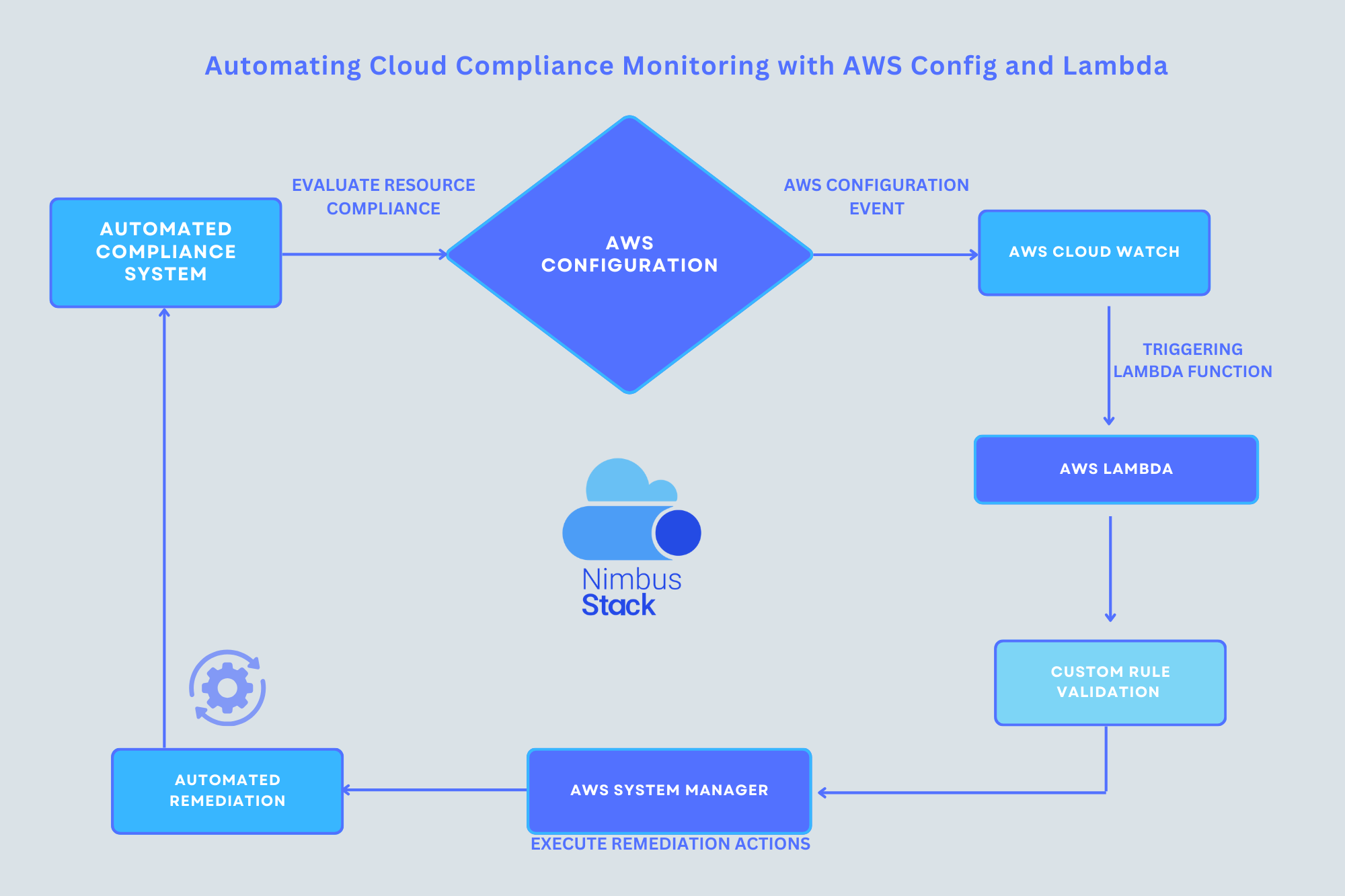
Maintaining compliance in the cloud is critical for ensuring security, governance, and adherence to industry standards. AWS Config, combined with AWS Lambda, provides a powerful solution for automating compliance monitoring in your AWS environment. By continuously tracking resource configurations an...