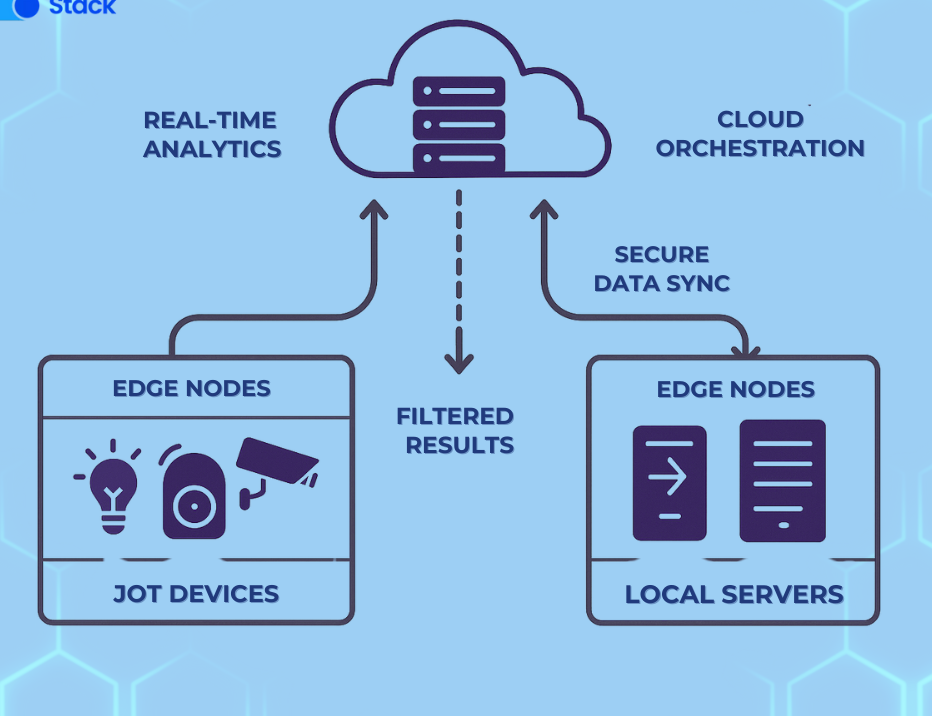
As microservices architectures grow in complexity, managing how services interact becomes increasingly challenging. Traditional approaches to service-to-service communication—once manageable in monolithic systems—now struggle to meet the demands of modern, distributed applications. That’s wher...
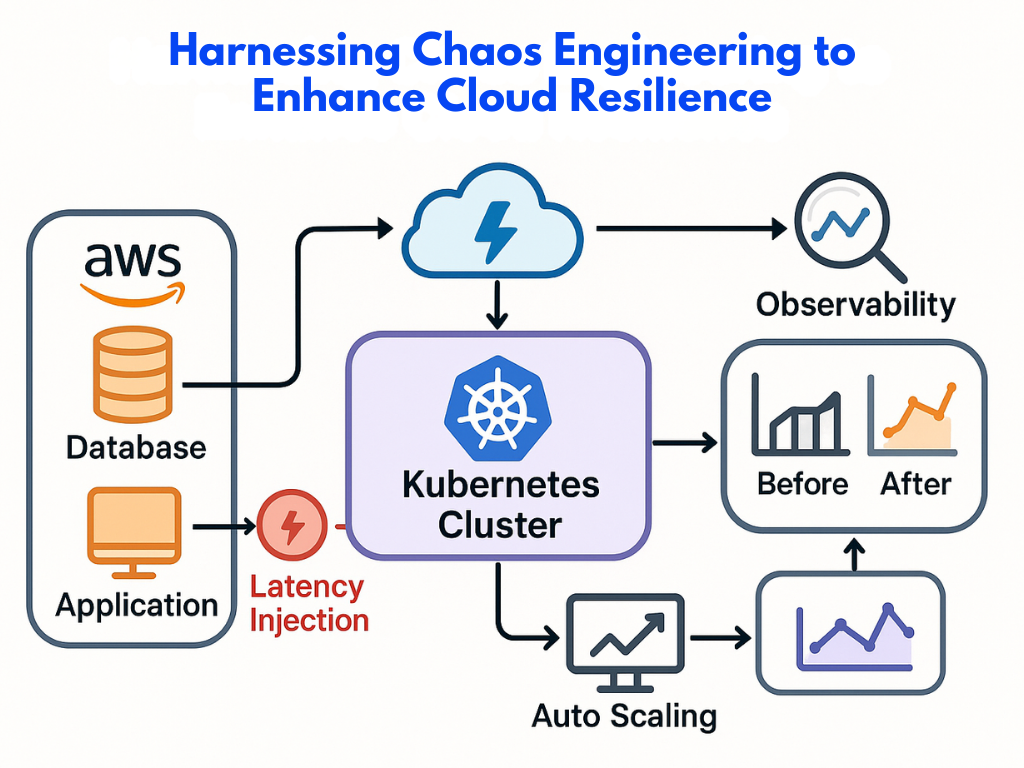
Modern cloud applications are designed for speed, flexibility, and scale—but with that complexity comes fragility. Unexpected outages, cascading failures, or misconfigured systems can bring even the most well-architected services to a halt. The solution? Break your own systems—before they break ...
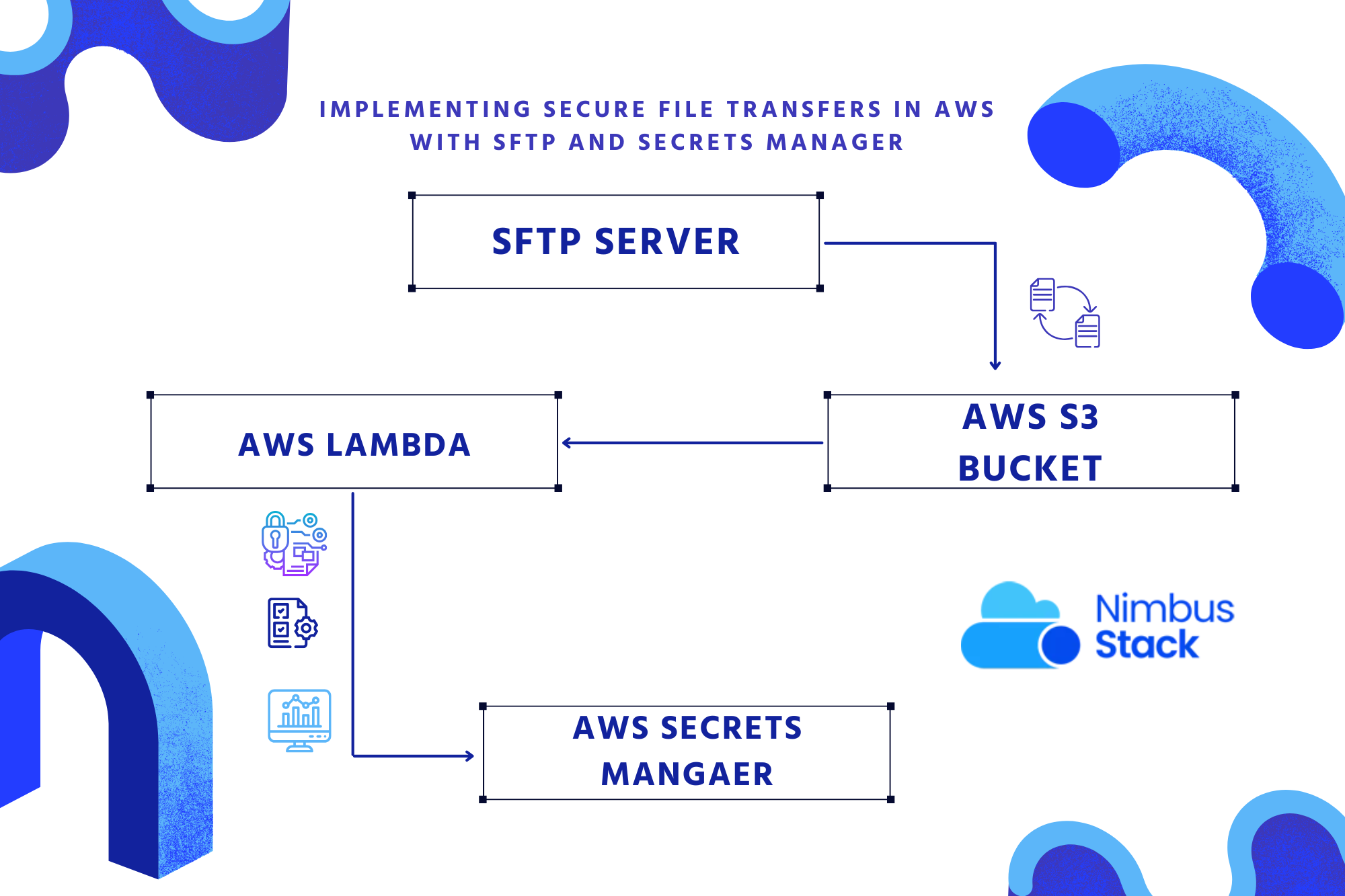
Secure file transfer is a critical requirement for organizations handling sensitive data. Whether transferring reports, logs, or customer records, a secure, scalable, and compliant solution is essential. AWS provides a robust framework for secure file transfers using AWS Transfer Family for SFTP (Se...
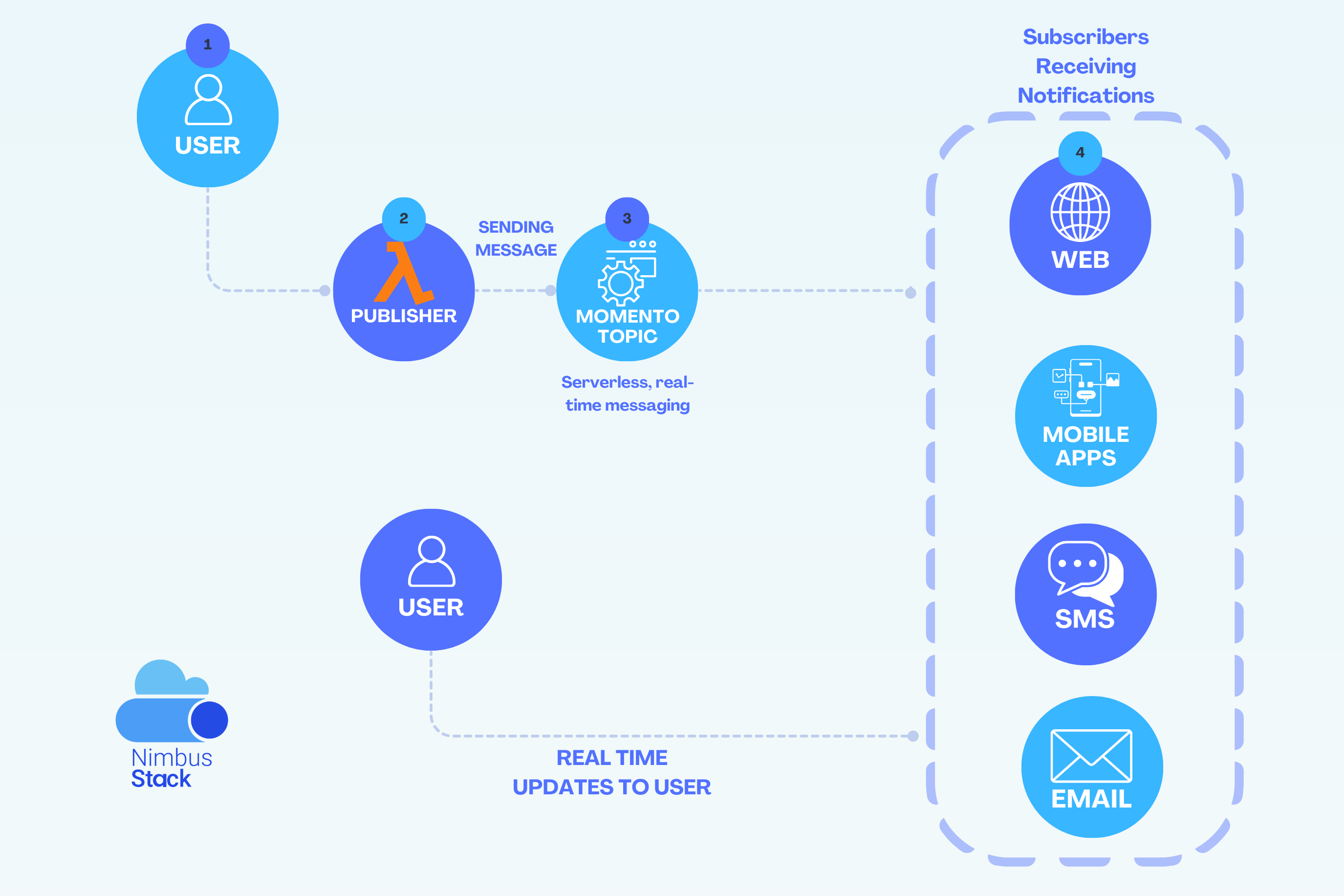
Real-time notifications are a cornerstone of modern applications, from chat systems and collaborative tools to e-commerce platforms providing instant updates. Implementing these notifications in serverless architectures can be challenging due to the need for scalability, low latency, and ease of int...
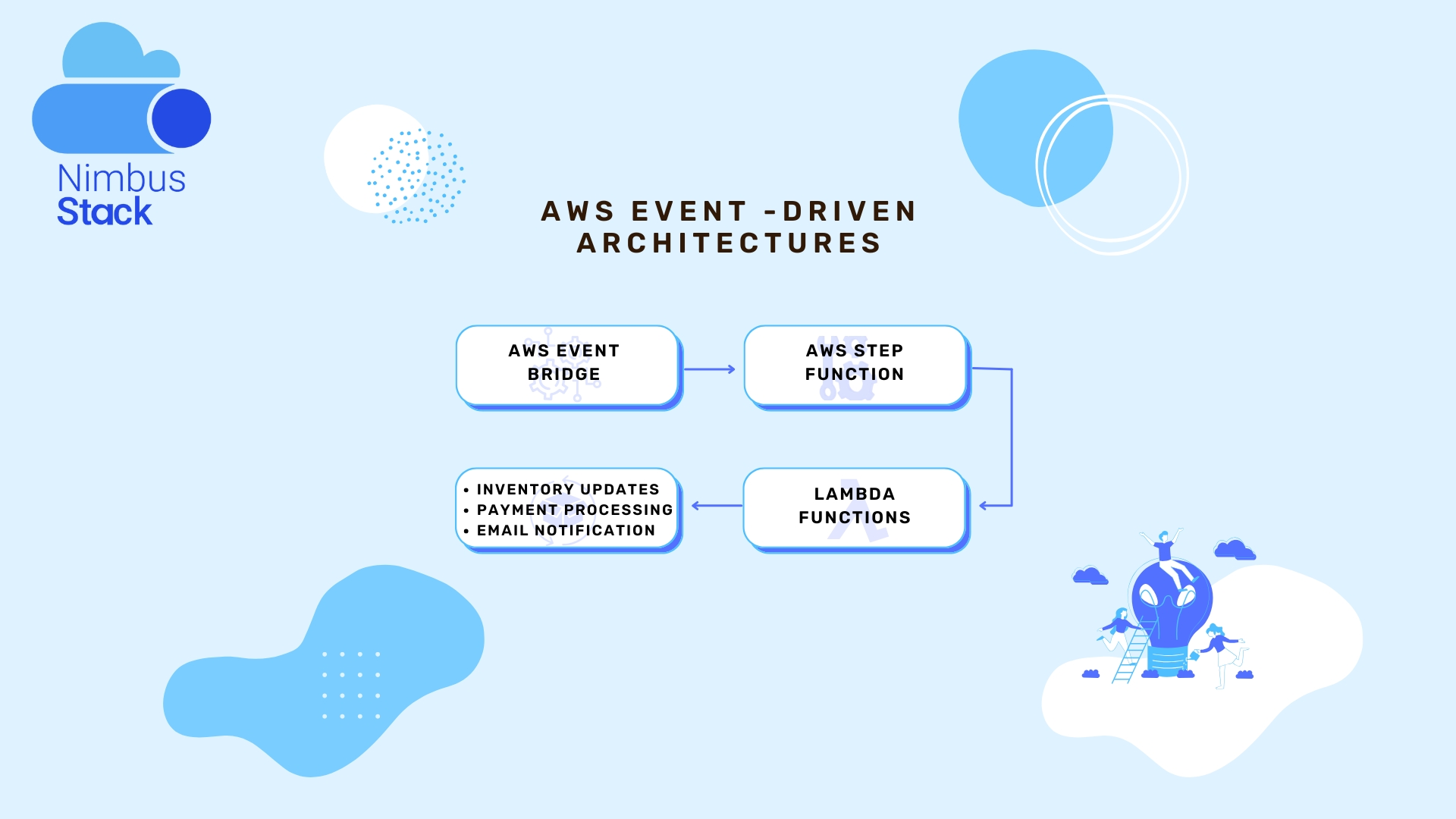
Event-driven architectures are at the heart of modern, scalable, and resilient cloud applications. By reacting to events in real-time, these architectures enable loosely coupled components that can independently process and respond to various triggers. AWS Step Functions and AWS Lambda are two essen...
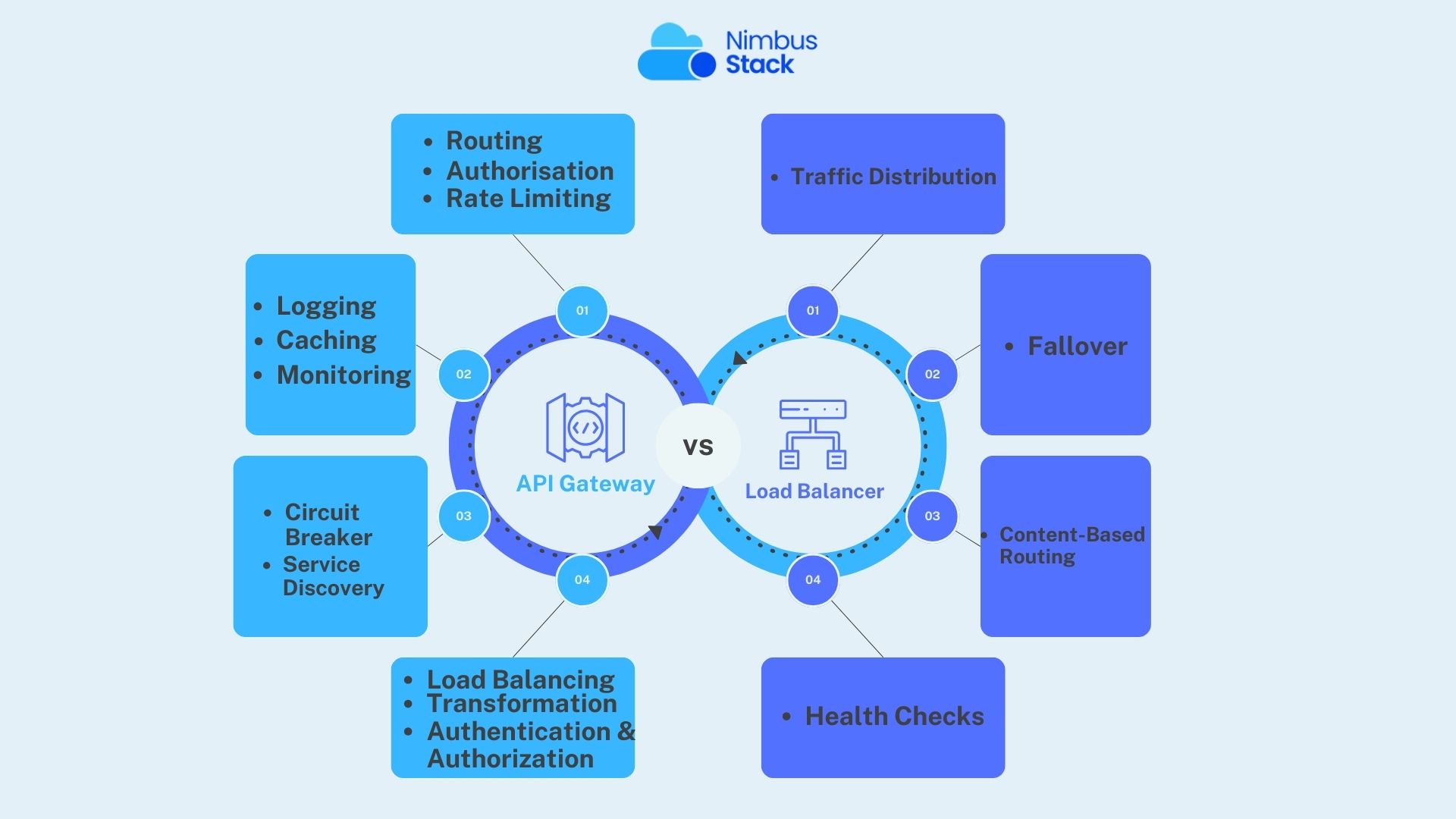
When building modern applications, you often need to manage how requests flow into your system. Two critical tools in this process are API Gateway and Load Balancer. While both play pivotal roles in handling client requests, they serve different purposes and are suited for distinct scenarios. In thi...
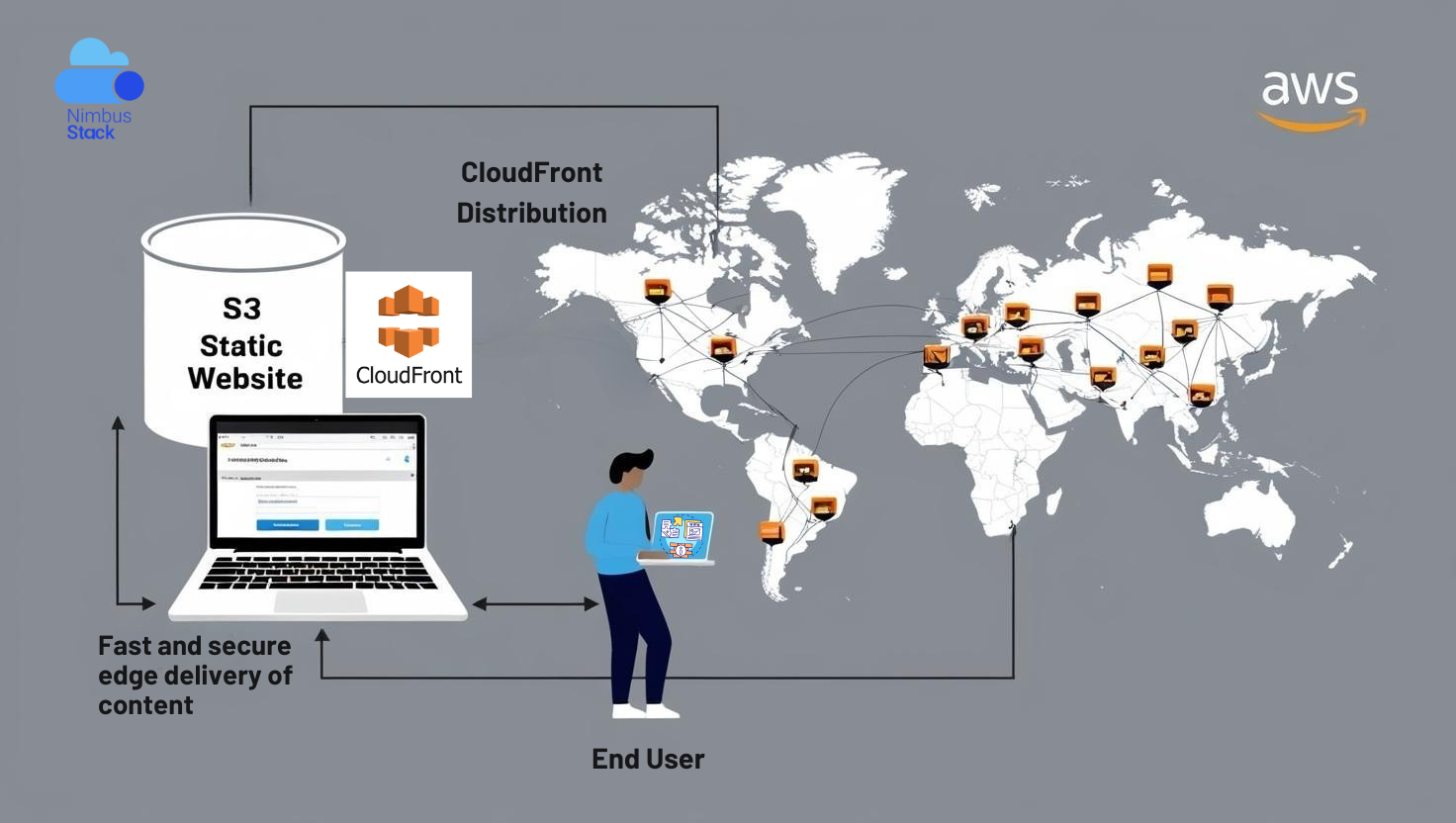
Hosting a static website on Amazon S3 (Simple Storage Service) combined with Amazon CloudFront (a Content Delivery Network or CDN) is a popular choice for achieving high availability, scalability, and low-latency content delivery. By leveraging these AWS services, you can ensure your website is fast...
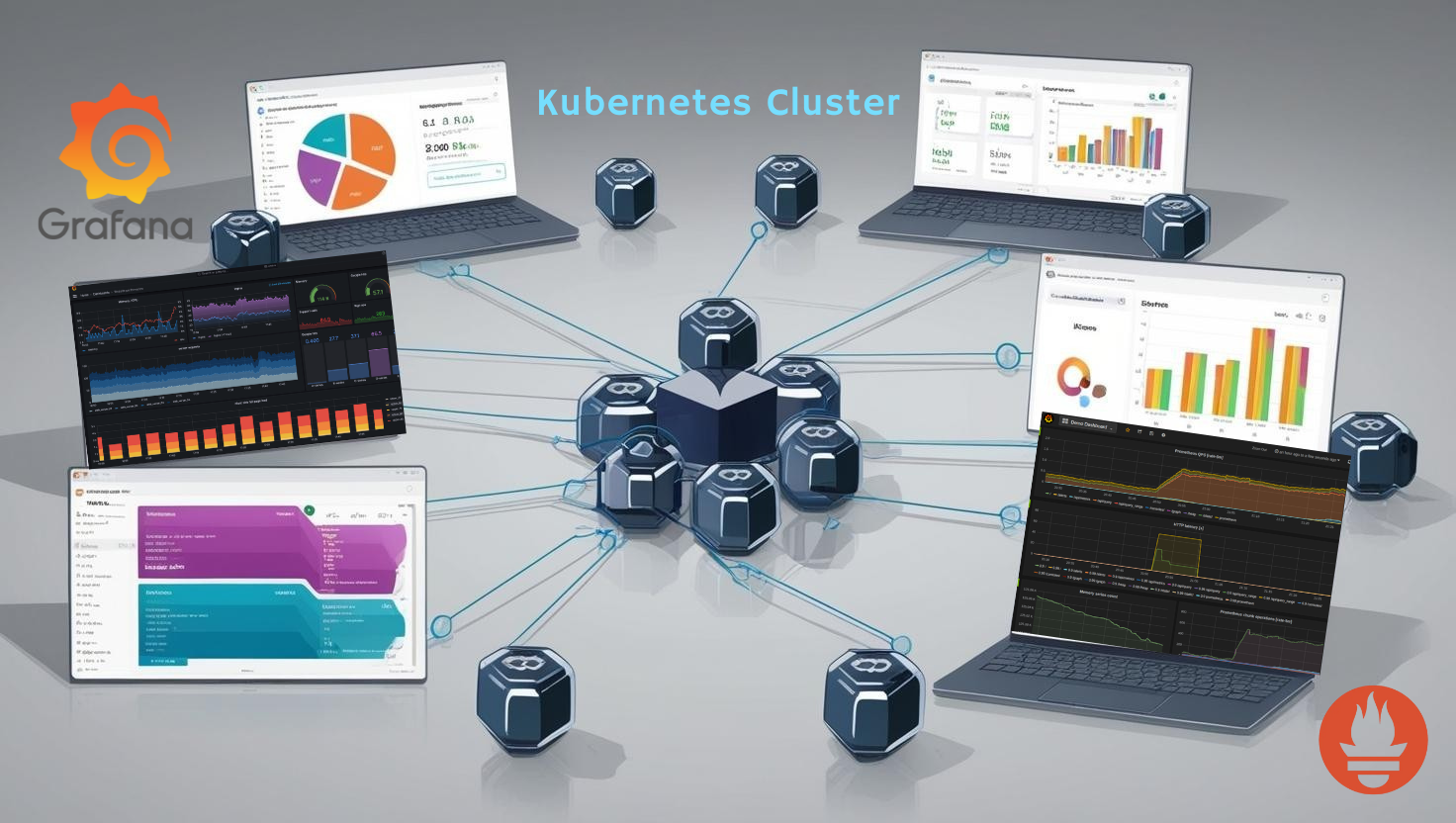
Kubernetes is the backbone of modern container orchestration, and Amazon Elastic Kubernetes Service (EKS) makes deploying Kubernetes clusters seamless. But with great flexibility comes the challenge of monitoring these clusters effectively. This is where Prometheus and Grafana step in as the ultimat...
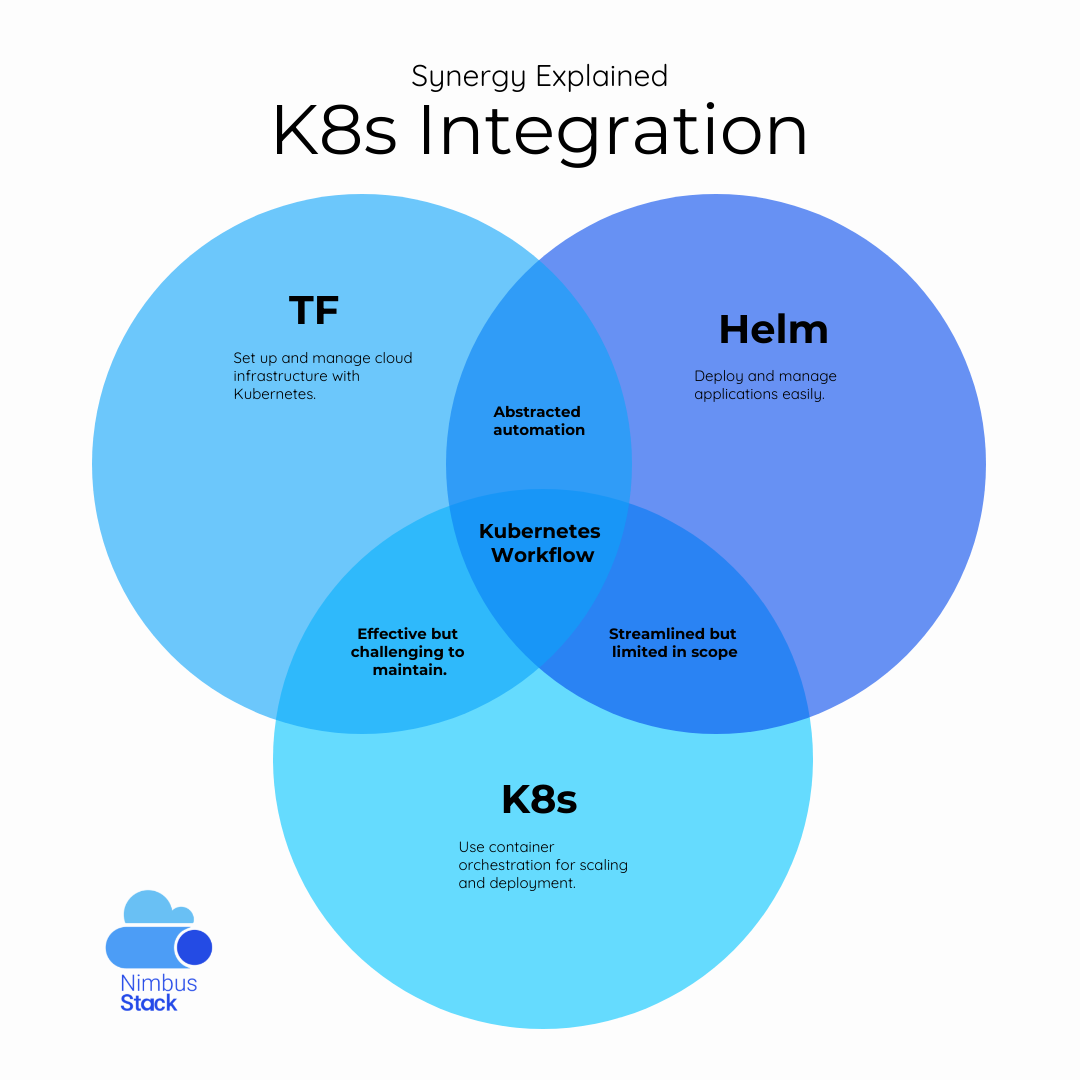
When managing Kubernetes-based applications and infrastructure, two powerful tools stand out: Helm and Terraform. Helm simplifies the deployment of applications in Kubernetes, while Terraform excels at managing infrastructure as code. Combining these tools can lead to a seamless, efficient, and scal...
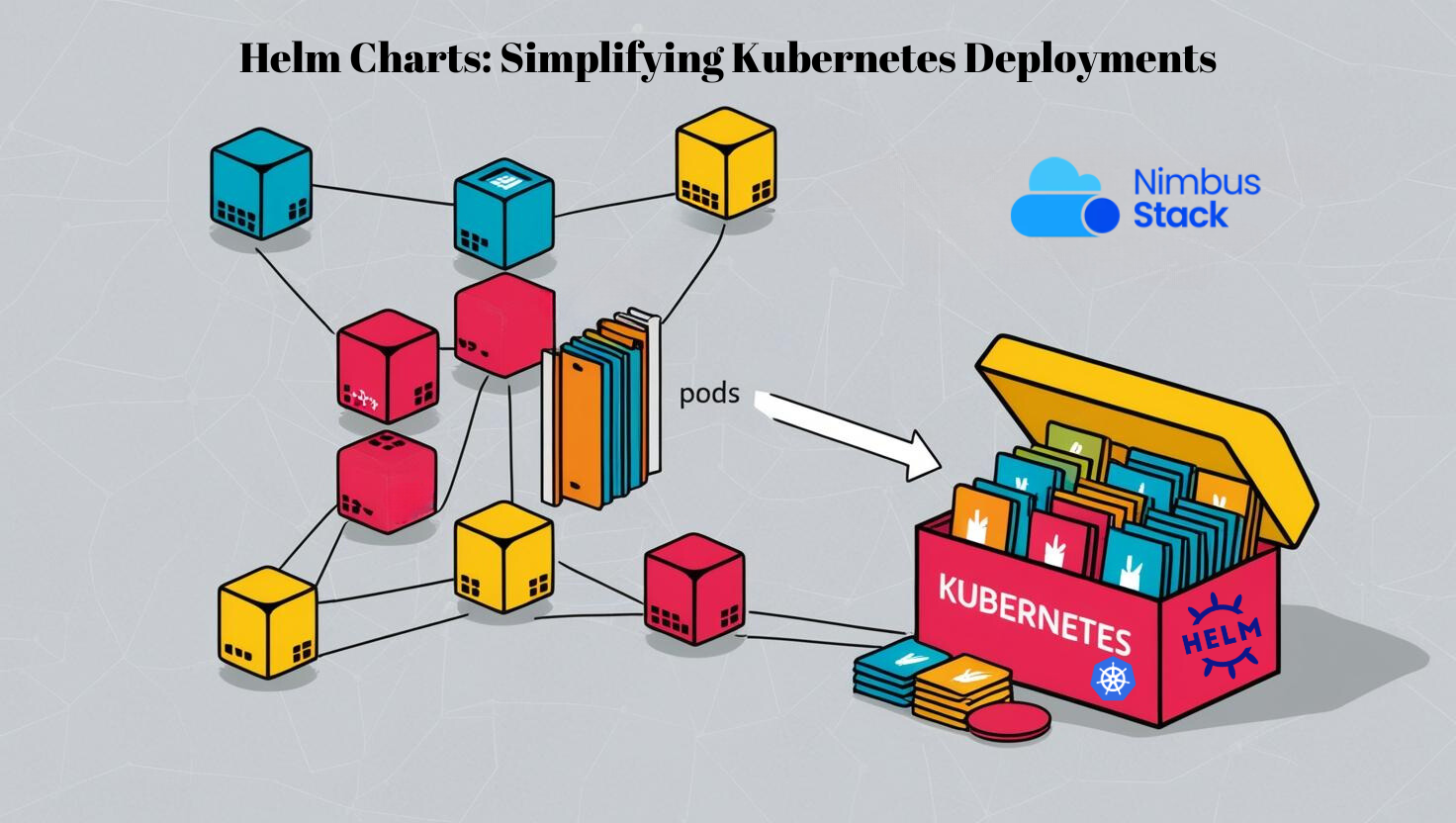
Managing Kubernetes deployments can sometimes feel like herding cats. You start with a couple of YAML files, then suddenly you’re juggling dozens of manifests for pods, services, and configurations. Chaos looms. That’s where Helm charts come in — the unsung heroes of the Kubernetes univers...